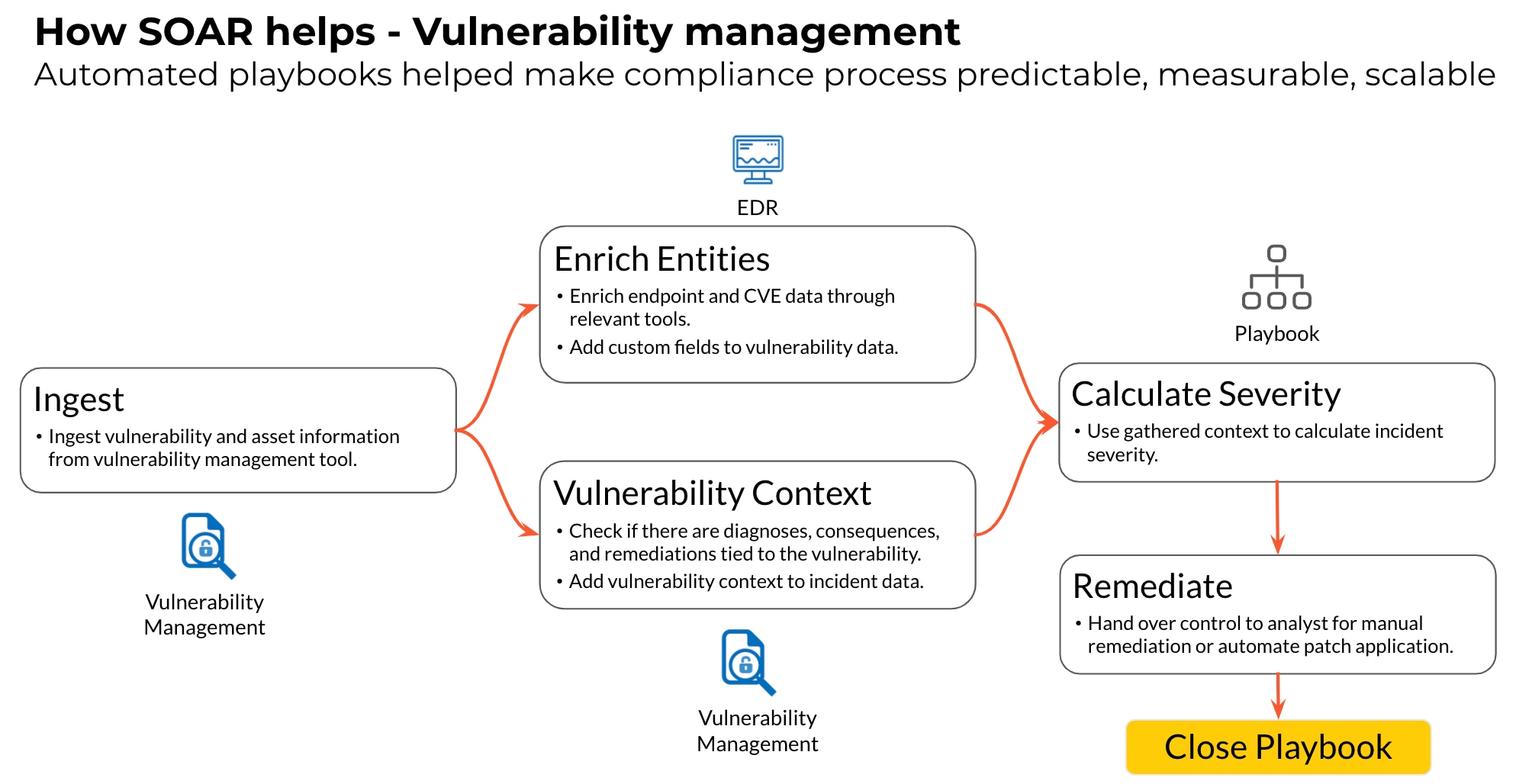
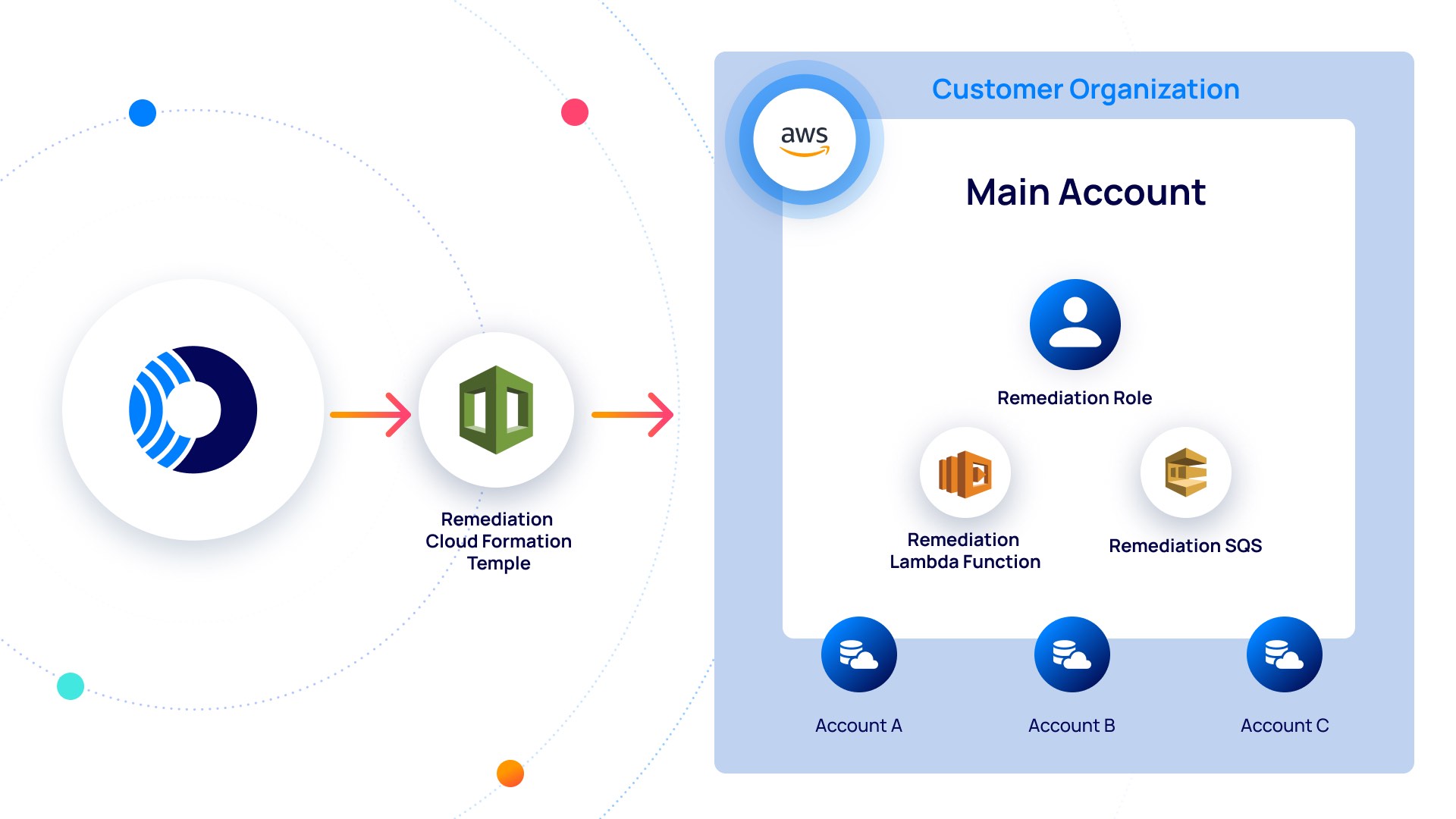
Rezillion Enhances Software Supply Chain Platform to Expand Detection, Prioritization and Remediation Capabilities, Bypassing Traditional Software Composition Analysis (SCA) Tools - Rezilion
Micro Focus and Keysight: Automatically Trigger Packet Capture to Accelerate Incident Remediation | Keysight