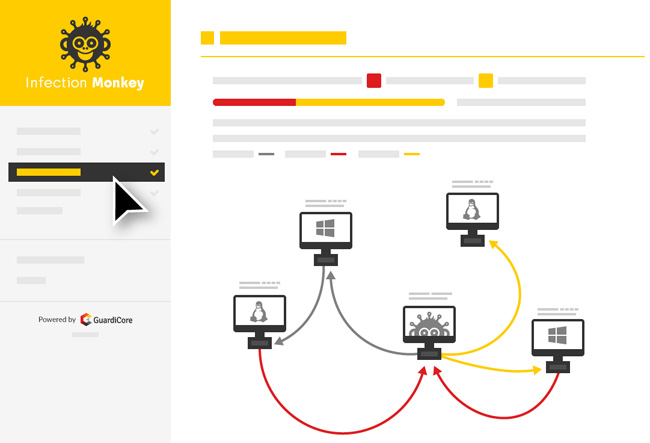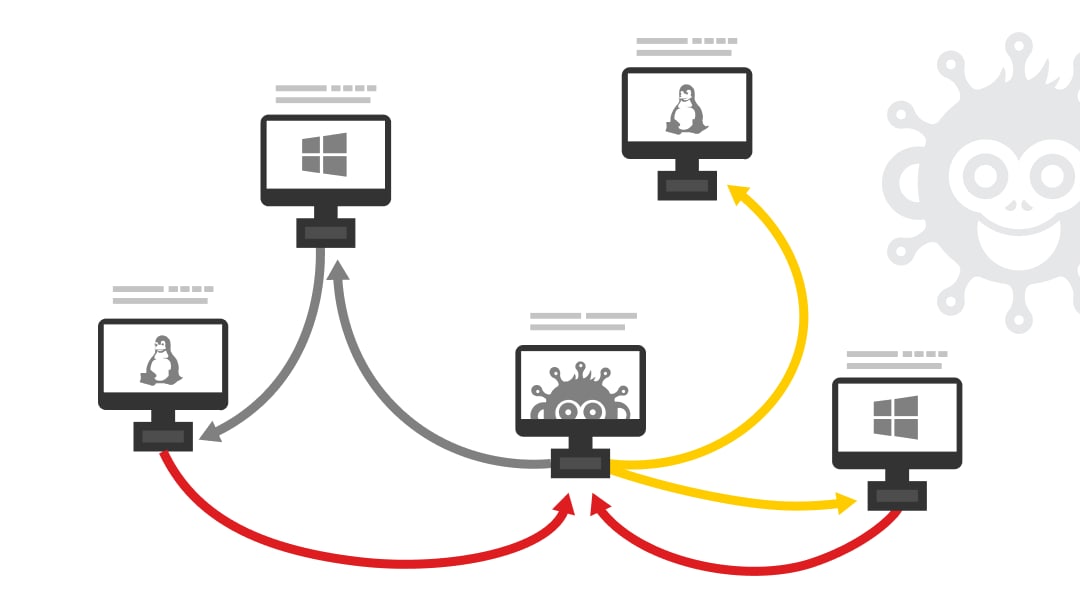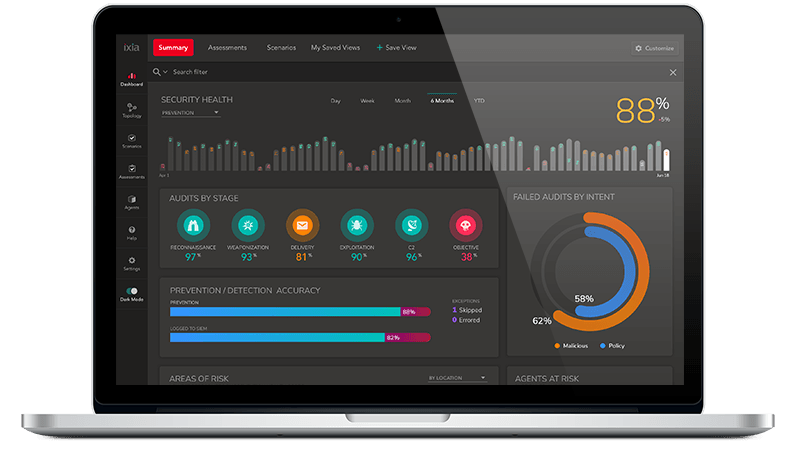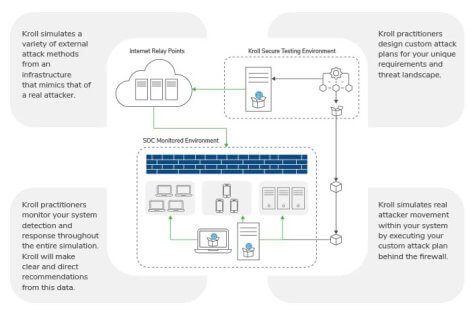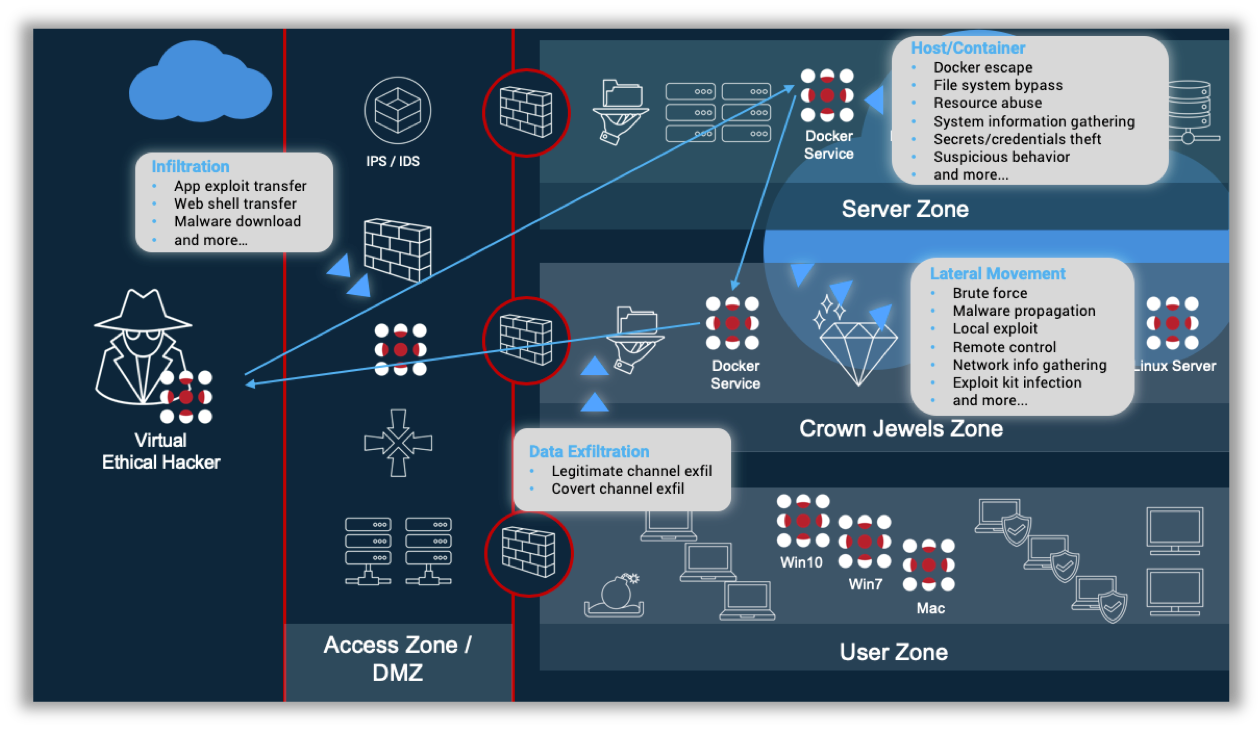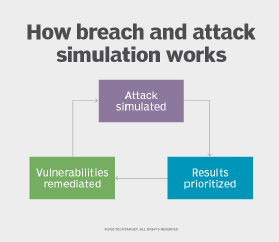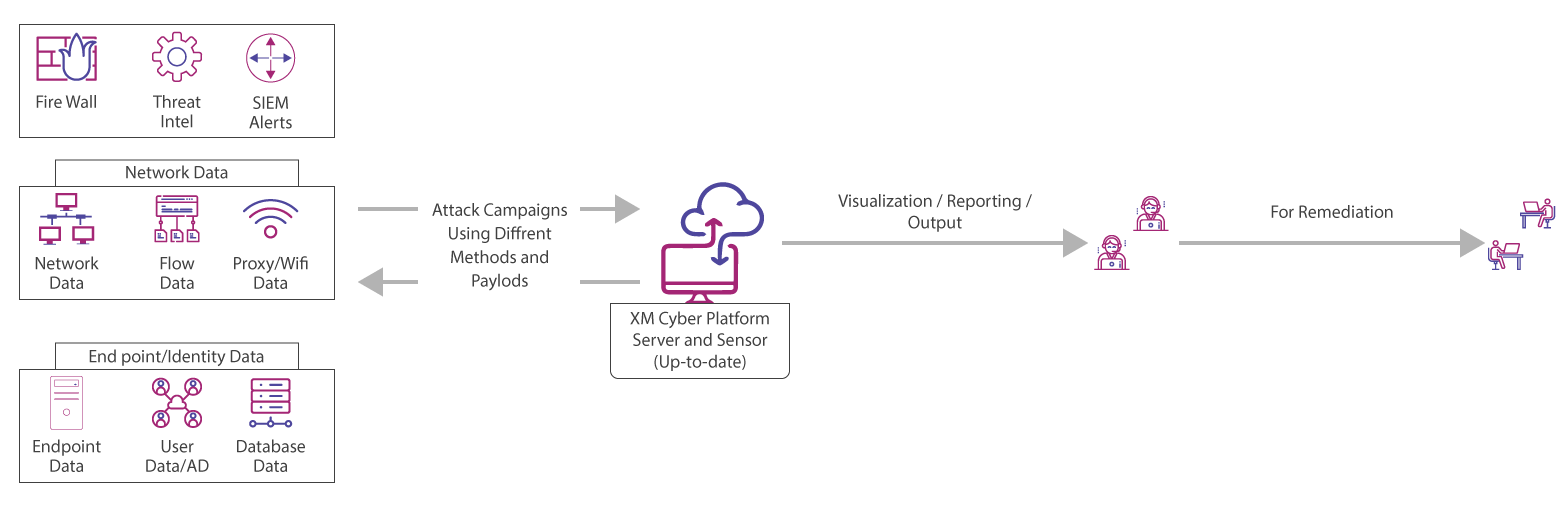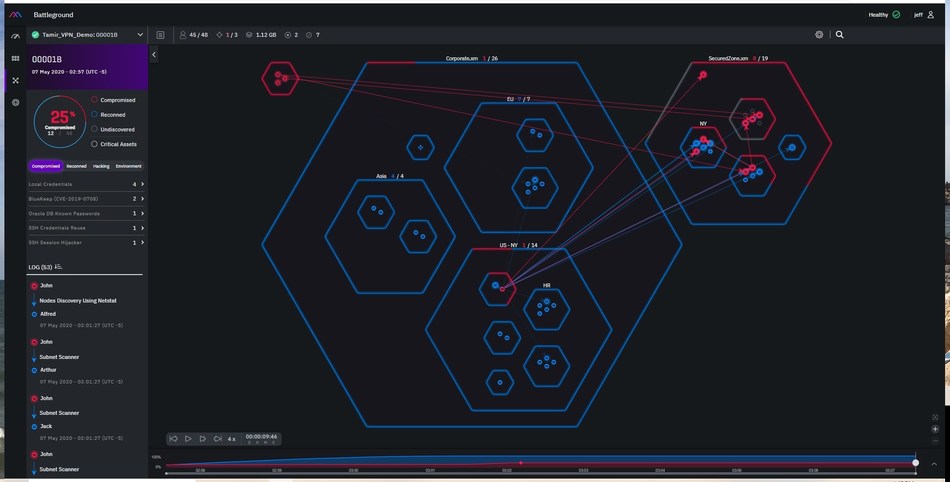
New Research Shows that Breach and Attack Simulation Technology is Key for Managing Cyber Risk in a World of Growing Complexity

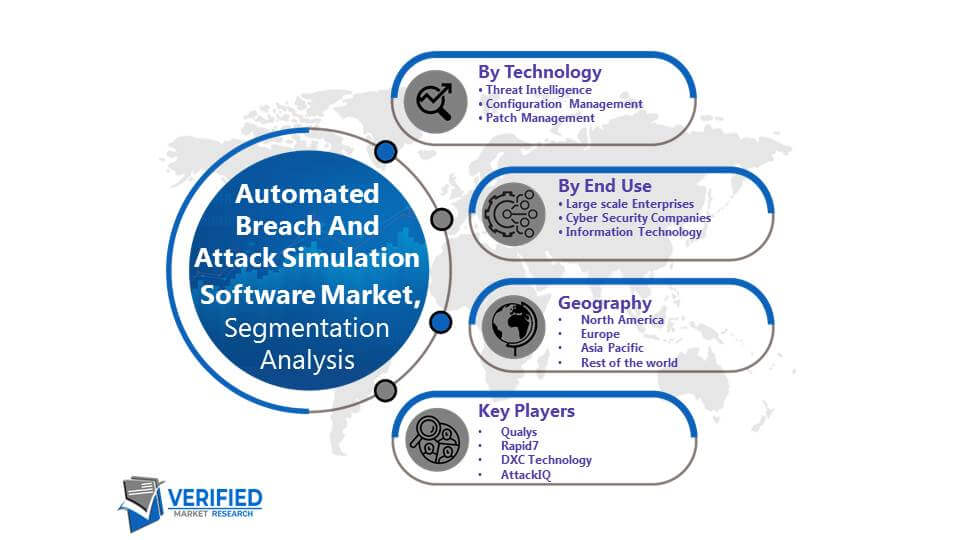
Global Automated Breach and Attack Simulation Market Outlook Report 2023-2029: Growing Complexities in Managing Security Threats & Growing Incidence of Data Breaches to Bolster Growth